BPCS Steganography To confirm that neither the embedding nor extracting processes harm the integrity of the payload, a small cover/vessel with visible watermark was prepared: GM vessel. This was then embedded with a payload of 3 files: an image file (JPEG), a text file, and an audio file (MP3), thus: [Click on image to view at full size]
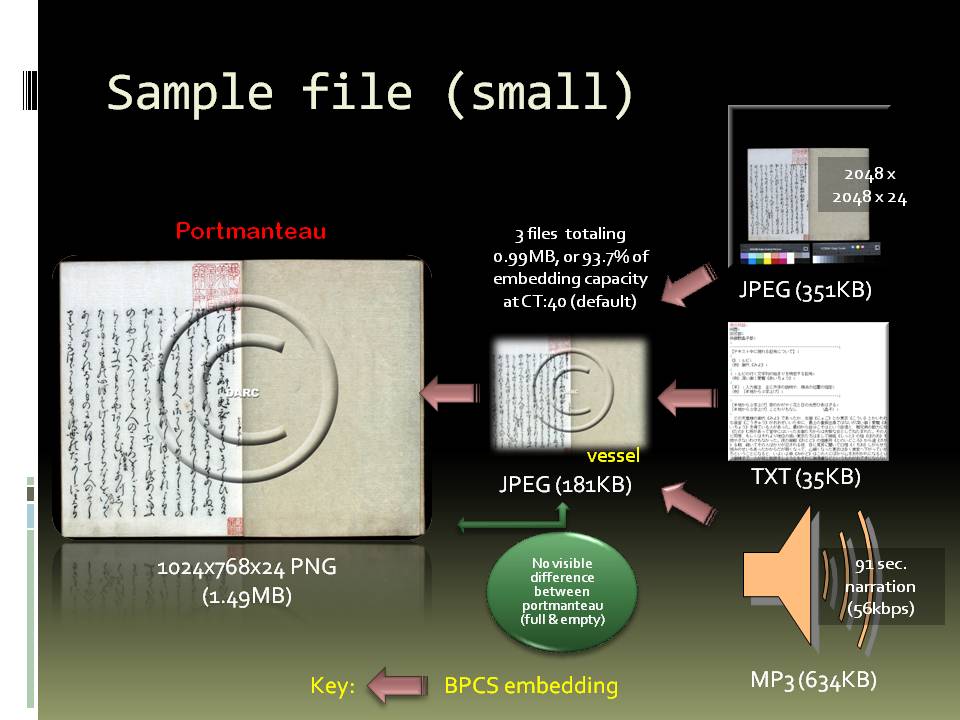
Embedding image, text & audio files in a small JPEG.
Since the cover/vessel file was small (181KB), for this experiment a high-resolution JPEG2000 image was not used as part of the payload, which was almost 1MB. Using Qtech-Hide&View's default complexity threshold of 40, it was possible to embed this payload without significantly degrading the quality of the cover image (see the final portmanteau file, 1.49MB). To confirm that the extracted files were identical to those originally placed in the payload, HashTab was used. This calculates the "fingerprint" of a file using 3 different mathematical calculations. No differences were found, either with this test file or others for which testing was repeated. What was discovered, however, is that as a result of the BPCS embedding process, cover/vessel image metadata is lost. Naturally, all metadata for the components of the payload is unchanged (as confirmed with the HashTab comparisons); it is only the outer "wrapper" that is affected, but this is not a problem as long as the metadata (TOC) is added after the portmanteau file is created. |