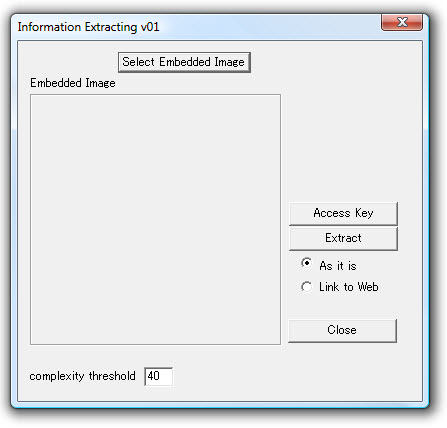
BPCS Steganography The extraction process requires that the complexity threshold be set to exactly the same value as was employed for embedding. While this might be considered an inconvenience, it is to be expected when using steganography: extraction always requires some prior knowledge of how the embedded data was encoded. It can also serve as sort of password, preventing casual access by those without permission (the CT value would only be sent to researchers who have been granted access). Generally speaking there are two approaches to steganography using image documents: image domain and transform domain. Image domain (or "bit-wise") tools such as Steganos manipulate the LSB of the cover image, replacing random noise with data. Transform domain software such as Digimarc, use DCT and wavelet transformations (like those employed for JPEG and JPEG2000) to embed a payload. Invisible watermarking, to conceal copyright and other information, is a type of steganography in which "survivability" is a key quality. Transform domain manipulation is more robust than LSB modification. When bit-wise steganography has been used to modify the LSB, the resulting file tends to have a different noise profile to others of a similar type. Statistical analysis of noise floor consistency and comparison with other files form the basis of the developing science of steganalysis. This field has grown in importance with the "war on terror", but while steganalysis may reveal the "fingerprint" or likely presence of embedded data, it is highly unlikely that it can actually find the data, especially if it has been encrypted. This, it must be stressed, is not a concern of the ADIEUX Project since the presence of the payload is not hidden; on the contrary, the payload is advertised in the metadata of the cover image. Organizations using steganalysis may decide that it is enough to destroy a suspected payload. Almost any editing of the image data, especially at the LSB level, is likely to render impossible the recovery of the embedded data. In the case of the ADIEUX Project, however, this can be seen as an advantage: any tampering with a portmanteau file is detectable. This essential "fragility" provides a way to confirm the integrity of an archival portmanteau. Returning to the Qtech-Hide&View application, the extraction process begins with selecting the portmanteau:
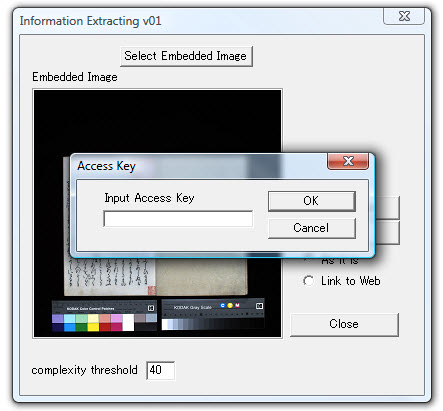
On the right is a button labeled "Access Key". This is a password required for extracting the payload. In other words, the recipient must have prior knowledge of (1) the fact that Qtech-Hide&View was used for embedding, (2) the complexity threshold used, and (3) the access key.
Here the access key function is disabled and thus no password is required for extraction. All that is needed is to click the Extract button. The file or folder is then fully accessible to the user; the portmanteau (stego) file remains intact. |